Monthly Archive:
November2022The CIA triad is a high-level checklist to evaluate security procedures. It is a vital model used to assess the risks, threats, and vulnerabilities of the system.
The CIA triad, also known as the AIC triad, is a benchmark model to assess Information Security. It guides security professionals in protecting any asset that is valuable for running a business.
Security testing should start from the requirement phase in the Software development lifecycle, and it should be integrated into every phase in SDLC.
CIA triad is helpful in identifying the information to be protected and in defining security requirements needed for an application.
CIA Triad stands for Confidentiality, Integrity, and Availability.
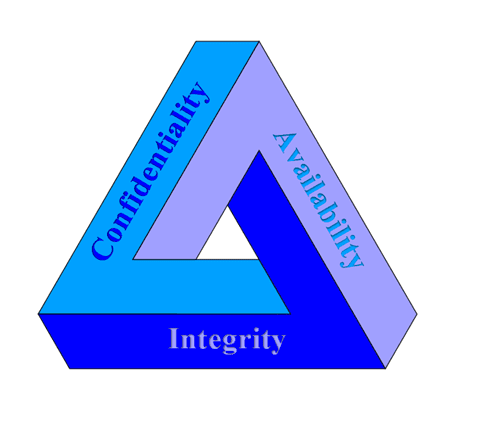
Confidentiality ensures that the system or data is exposed to the right users. This could be ensured by having the following four security measures in an application. They are Identification, Authentication, Authorization, and Encryption.
The confidentiality of an application is assessed by knowing whether the sensitive information in a system is disclosed to unauthorized users. The sensitivity of data is a measure of its importance. The owner of the data decides the sensitivity measure of the data.
Integrity ensures that the data is reliable. The system or data should be accurate, complete, and consistent.
The integrity of the data could be ensured by having proper security measures in our system. Some of them are Hashing, User access controls, Version control, Backup and recovery procedures, Error checking, and Data validation.
The integrity of the data is measured using a factor called the baseline. The baseline is the measure of the current state of the data. The goal of integrity is to preserve the baseline throughout the transaction.
The data or system should be available to the users when and wherever it’s needed. The availability of the application could be ensured by using Hardware maintenance, Software patching/upgrading, Load balancing, and Fault tolerance.
Appropriate levels of availability should be provided based on the criticality of the data. Criticality is the measure of the dependency of a system on data to perform its operation.
CIA triad helps in understanding and prioritizing the severity of a vulnerability in an application. Neglecting the CIA triad makes the application vulnerable to Interruption, Interception, Modification, or Fabrication class of attack.
CIA serves as a yardstick to evaluate the security of an application. If CIA triad standards were met, then the security of that system would be stronger and better equipped to handle threats.
Is CIA Triad enough for Information Security? – No, but it covers most of the security loopholes in an application.
Authored by Shamphavi Shanmugasundram @ BISTEC Global